Talere i verdensklasse
Brancheførende eksperter deler erfaringer og fremtidsperspektiver.
Velkommen til Identity Day! Efter stor succes i Sverige og Finland, er vi nu glade for endelig at bringe eventet til Danmark.
I Sverige og Finland har vi de seneste år haft fornøjelsen af at samle nogle af branchens førende eksperter inden for Identitetssikkerhed, og sidste år kunne vi byde over 500 deltagere velkommen til vores events. Nu får Danmark også chancen for at deltage i årets mest inspirerende event.
På Identity Day deler eksperter indsigt, værktøjer og strategier til at beskytte din organisation mod cybertrusler og databrud. Du vil få mulighed for at høre inspirerende oplæg om de nyeste tendenser og kommende udfordringer, og lære, hvilke løsninger der er mest effektive for at styrke din organisations sikkerhed.
Få dybdegående ekspertviden inden for vigtige områder som IAM, IGA, PAM, AM og meget mere.
Det er den perfekte mulighed for at netværke med branchekolleger og nyde god mad og drikke – helt gratis.
Book din plads og vær med til årets mest inspirerende event!


Brancheførende eksperter deler erfaringer og fremtidsperspektiver.
Lær nye ting og få værktøjer, du kan tage med tilbage til dine kolleger.
Skab nye forbindelser med andre i branchen og udbyg dit netværk.
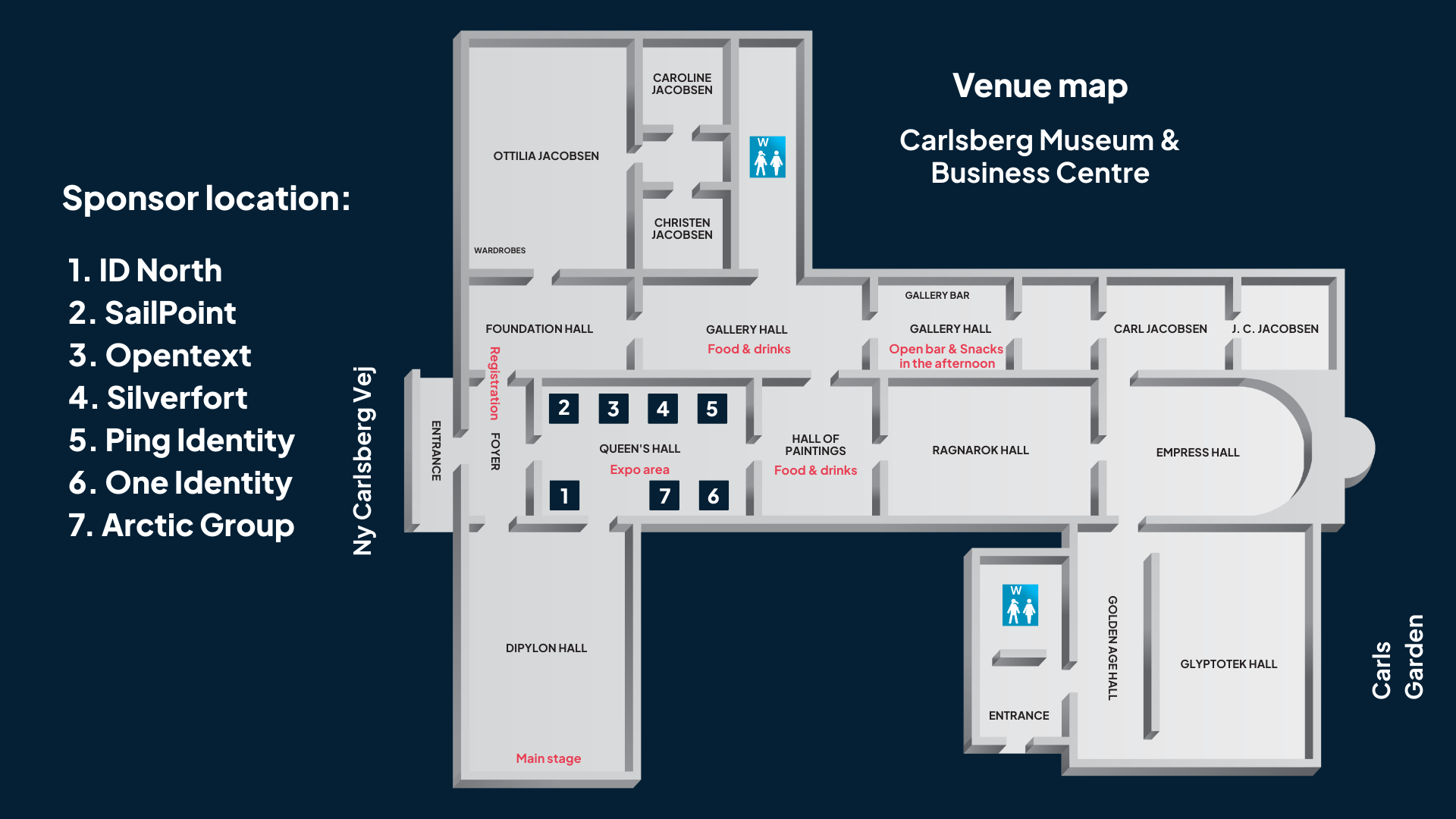
Vi ses i de hyggelige og inspirerende lokaler på Carlsberg Museum & Business Centre.
Dagen byder også på en spændende, valgfri guided tur i Carlsberg Museum.
Lækker mad og drikke serveres hele dagen og aftenen.

Moderator
Gitte Gormsen has worked with Identity & Access Management for the past five years, focusing on marketing activities and business development within the domain. She has engaged in the cybersecurity, GRC and compliance agenda for more than 10 years. She has run professional IAM client communities, published articles and newspaper inserts on the IAM agenda and headed up some of the most successful IAM events on the Danish scene. Gitte will be guiding you through the day and make sure you leave with a firm overview of the learnings brought to you by the leading tech providers in the market.

Have we lost our Identity in a world of compliance?
Identity is more critical than ever, it’s the foundation of who we are, guiding our values, decisions, and interactions with the world. Within the context of compliance and digital security, identity becomes even more significant. In a world where personal data is constantly at risk of being hacked or manipulated, maintaining a clear and secure sense of identity is essential to protect not just our personal information, but our autonomy and control.
With over 20 years of experience in Identity and Access Management (IAM), Sören specialize in Identity Lifecycle Management, Identity Governance, and Zero Trust Architectures.

"How Non-Human Identities Create Operational and Cyber Risk for Organisations"
Non-Human Identities (NHIs) pose one of the most significant cyber threats to an organisation as they can pose severe operational risks. In many cases, NHIs have elevated privileges, lack proper oversight, are not documented, and are often not linked to specific individuals. This makes them attractive targets for attackers, who may exploit them to gain unauthorised access, move laterally within systems, and carry out malicious activities without being detected. In our session, Silverfort will examine how organisations can reduce operational risk by understanding and implementing security controls around their Non-Human Identities.
Key Takeaways:
Regional Sales Manager at Silverfort.

"Enabling Continuous Trust Through Verifiable Credentials, Low-Friction Authentication, and Identity Verification"
Traditional perimeter-based identity models are no longer sufficient in an environment where threats are persistent, identities are dynamic, and user interactions span multiple devices and platforms. This technical workshop will dive deep into how continuous trust models can be architected using decentralized identity technologies, low-friction authentication mechanisms, and real-time verification process.
Steven Hayhoe is a seasoned identity and cloud specialist with over two decades enabling large scale, secure digital transformations across a range of industries including financial services, government, and critical infrastructure. As Principal Solution Consultant at Ping Identity, he helps global organisations design and implement resilient, secure and scalable IAM solutions that support workforce, customer and B2B IAM use cases.

"Tomorrow will be different"
The future is spelled A.I., and it’s rewriting Identity Security in more ways than we dare to admit.
Get ready for a thought-provoking journey from the messy present to the autonomous future of Identity. This talk explores the explosive evolution of both AI and Identity Security, challenging us to look beyond today’s manual toil and into a redefined world powered by AI Native technology.
Sami Mäkelä, CTO at ID North, brings nearly 30 years of experience in system development, IT risk, and security. His expertise spans Identity and Access Management (IAM), Security Information and Event Management (SIEM), Identity & Access Governance, as well as risk and quality metrics. Throughout his career, Sami has combined deep technical knowledge with strategic insight to deliver secure, scalable, and future-ready solutions.

"Why the Identity Graph is key to the future of Identity Security"
Mikael Wikström works as a Cyber Security Technical Advisor covering the Nordics region where he assists enterprises and organizations in defining the strategy and adoption of an integrated Identity Governance Platform. Mikael has more than 30 years experience in the Cyber Security software industry, where he has lead teams in the development and implementation of complex Cyber Security solutions with a focus on Identity Governance, Identity Management, Access Management in a wide range of organizations and enterprises.

“An Identity Security Fabric is no longer optional"
An Identity Security Fabric is no longer optional—it’s essential for protecting access across IT, OT, DevOps, multicloud, AI, and non-human identities while meeting growing regulatory demands.
Too often, security tooling and teams operate in isolation from PAM, IGA, Access Management, AD security, and other controls, creating blind spots and inconsistent policies.
The result? Limited visibility, fragmented accountability, and unanswered questions about who has access to what, how, and why.
Join this session to learn how the One Identity Fabric unifies security silos, strengthens compliance, and delivers 360° oversight of all identities and entitlements—human and non-human alike.
As an evangelist and innovator, helping the c-suite understand the business value of a digital transformation journey. Alan assist in creating strong security strategies and roadmap to protect the most valuable assets in people, process and technology.
Passionate about the technology he has worked with over the past 20 years, Alan consider himself privileged in having a profession that he also enjoys in his spare time.

"Weaving the Future"
Identity is no longer an IT side note it’s the foundation of digital trust and business growth.
This session uncovers how Identity Fabric turns today’s fragmented systems into one unified strategy, driving ROI, agility, and resilience in the AI era. The organizations that master it will lead. The rest will be left unraveling the loose threads.
With over 25 years in B2B sales, Anders Rönnquist specializes in innovative IT solutions, particularly in identity and access management (IAM) and security. His strategic approach enhances business efficiency and drives digital transformation. As a trusted advisor and strategic partner, Anders and his team ensure secure access and protection of sensitive information. He leads the sales team to drive revenue growth, expand market share, and align business development initiatives with organizational goals.

"Hidden Dragon: A Thriving Chinese Fraud Ecosystem"
Dive into a complex ecosystem representing a massive threat in the fraud space. Gain a deeper understanding of the components, services, actors, and trends of the growing Chinese criminal underground. Supported by and built on top of nearly 2 years of research into the Chinese smishing syndicates who pioneered the use of Digital Wallets to enable fraud, we’ll focus on the entire ecosystem’s evolution and supporting pillars. This presentation will cover major actors, services on offer, trends in targeting, monetization, money laundering, and more.
With a foundational career spanning over a decade as a Senior Architect securing Linux and BSD systems within datacenter and hosting environments, Ford contributed notably to the defense of the American Financial sector during ’Operation Ababil’ between 2012-2013. His efforts in disseminating live attack data and insights greatly benefited the security community and culminated in a pivotal presentation at ISOI 11 in Burbank. In 2014, Ford embraced a move from Texas to pursue a dedicated cybersecurity research role at CSIS Security Group in Copenhagen, Denmark, continuing deeper research into DDoS actors, malware, brand infringement, phishing, and conducting incident response activities. Notably, Ford was the principal developer behind the technology stack that powers the CSIS Anti-Phishing service, phishdb.

We start the day with breakfast and networking.

Our moderator Gitte Gormsen will start the day in Dipylon Hall.

Non-Human Identities (NHIs) pose one of the most significant cyber threats to an organisation as they can pose severe operational risks. In many cases, NHIs have elevated privileges, lack proper oversight, are not documented, and are often not linked to specific individuals. This makes them attractive targets for attackers, who may exploit them to gain unauthorised access, move laterally within systems, and carry out malicious activities without being detected. In our session, Silverfort will examine how organisations can reduce operational risk by understanding and implementing security controls around their Non-Human Identities.

Identity is more critical than ever, it’s the foundation of who we are, guiding our values, decisions, and interactions with the world. Within the context of compliance and digital security, identity becomes even more significant. In a world where personal data is constantly at risk of being hacked or manipulated, maintaining a clear and secure sense of identity is essential to protect not just our personal information, but our autonomy and control.

Traditional perimeter-based identity models are no longer sufficient in an environment where threats are persistent, identities are dynamic, and user interactions span multiple devices and platforms. This technical workshop will dive deep into how continuous trust models can be architected using decentralized identity technologies, low-friction authentication mechanisms, and real-time verification process.

Mingle & coffee in Queens Hall.
Take the opportunity to visit the sponsors in their stands during break.

Dive into a complex ecosystem representing a massive threat in the fraud space. Gain a deeper understanding of the components, services, actors, and trends of the growing Chinese criminal underground. Supported by and built on top of nearly 2 years of research into the Chinese smishing syndicates who pioneered the use of Digital Wallets to enable fraud, we’ll focus on the entire ecosystem’s evolution and supporting pillars. This presentation will cover major actors, services on offer, trends in targeting, monetization, money laundering, and more.

The future is spelled A.I., and it’s rewriting Identity Security in more ways than we dare to admit.
Get ready for a thought-provoking journey from the messy present to the autonomous future of Identity. This talk explores the explosive evolution of both AI and Identity Security, challenging us to look beyond today's manual toil and into a redefined world powered by AI Native technology.

- Learn why governance and security always starts with insight.
- Discover how a modern data model strengthens identity security.
- Hear how a platform approach simplifies and enhances identity management.
- Learn from the leader in Identity Security why this is just the beginning – and find out what’s next for identity security.

Enjoy tasty mini versions of the Danish classic “smörrebröd” - and take the chance to meet our sponsors at their stands during lunch.

An Identity Security Fabric is no longer optional—it’s essential for protecting access across IT, OT, DevOps, multicloud, AI, and non-human identities while meeting growing regulatory demands.
Too often, security tooling and teams operate in isolation from PAM, IGA, Access Management, AD security, and other controls, creating blind spots and inconsistent policies.
The result? Limited visibility, fragmented accountability, and unanswered questions about who has access to what, how, and why.
Join this session to learn how the One Identity Fabric unifies security silos, strengthens compliance, and delivers 360° oversight of all identities and entitlements—human and non-human alike.

Identity is no longer an IT side note it’s the foundation of digital trust and business growth.
This session uncovers how Identity Fabric turns today’s fragmented systems into one unified strategy, driving ROI, agility, and resilience in the AI era.
The organizations that master it will lead.
The rest will be left unraveling the loose threads.

Discussion with our experts from SailPoint, Ping Identity, Opentext, Silverfort and One Identity on stage.

Enjoy drinks & snacks while you take the opportunity to visit the sponsors in their stands during mingle.

Optional guided tour of Carlsberg Premises.




















Arctic Group er Nordens førende eksperter inden for Identitetssikkerhed & Cybersikkerhed. Vi er din langsigtede partner i din digitaliseringsrejse – vores ekspertise hjælper dig med at sikre fremtiden. Vær sikker sammen med os!

Vi hos ID North er specialiseret i identitetssikkerhed og hjælper din virksomhed med at beskytte jeres digitale identiteter. Hos os får du adgang til branchens førende eksperter. Vore løsninger sikrer effektivitet, omfattende kontrol og beskyttelse på højeste niveau. Sikr din organisations fremtid sammen med os.
Ja! Selvom eventet er gratis, vil vi gerne minde om, at der kræves tilmelding for at deltage. Vi ser virkelig frem til at byde jer velkommen og ønsker at sikre, at alle får en fantastisk oplevelse!
Nej! Da det er et gratis event, har vi et begrænset antal pladser. Vi vil ikke kunne tage imod tilmeldinger på stedet under eventet, så sørg for at sikre din plads allerede i dag!
Eventet er åbent for alle virksomheder og organisationer, der opererer i digitale miljøer. Arbejder I med hybride arbejdspladser? Har du en digital profil? Håndterer I personlige data? Så er identitetssikkerhed af største relevans.
Selvfølgelig, sørg bare for at tilmelde jer, så der er den rette mængde mad og pladser. Tag en ven eller kollega med og tilmeld jer i dag.
Netværk, mad & mingling. I løbet af dagen og aftenen får du også mulighed for at skabe nye forbindelser i branchen, blive underholdt og nyde lækker mad.
Eventet afholdes på dansk med indslag af præsentationer, der vil blive holdt på engelsk.